|
Now that you've read the The Complete Guide to Customer Research Interviews, you know that gathering intelligence from customer interviews, market analysis, online research, win/loss analysis, is critical to developing a strategy that drives product-market fit and growth. But once you have accumulated all your customer and market insights, what do you actually do with it? Here are 5 immediate steps to infuse your strategy with intelligence in practice.
0 Comments
A company is only as secure as its weakest link. But what if the weakest link isn't at the company at all, but rather one of its third-party vendors? A company can reinforce its own security posture by training its staff and implementing the latest tech, but it still has to provide access and share information with its suppliers, and its suppliers’ suppliers, and so on along the chain. With each degree of separation, the company has less control over its suppliers’ security – especially small suppliers lacking security controls. But when there is a data breach, no matter how far along in the supply chain (e.g. even if it's your vendor's vendor's vendor), you yourself bear the consequences.
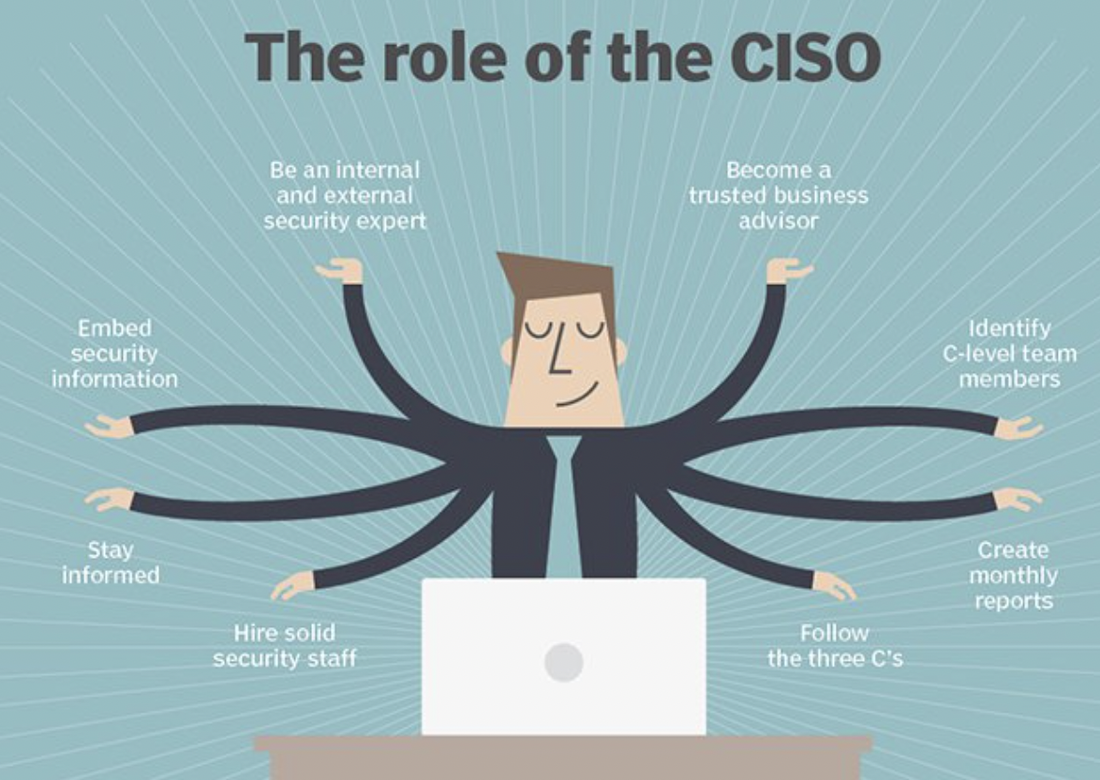
Last year I was fortunate to attend several all-day Chief Security Officer (CISO) roundtables on data protection with some of the top CISOs from Fortune 500 and beyond. Imagine being the CISO of a huge company like Honeywell with over 100,000 employees made up of hundreds of loosely coupled acquisitions worldwide, or Thales, a $17B organization and itself an industry leader in security. Imagine being the CISO of one of the major international banks like JP Morgan. As the CISO, what would be most on your mind? What would be keeping you up at night? Here are the 5 recurring themes I heard.
Enterprise IT leaders are migrating existing software applications to the cloud. There are benefits to moving to the cloud, but many risks in getting it done right, in a way that doesn't interrupt business operations or introduce regression in functionality.
Below is a guide for projects managers and product owners for structuring cloud onboarding projects. It can be encouraging and disappointing all at once if your team has worked hard to generate marketing qualified leads (MQLs) but somehow they just aren’t converting to actual revenue. For SaaS stores, this can look like lots of sign-ups but few actual transactions. In a traditional B2B company, you might see a lot of activity - website visitors, webinar attendees, trade show booth visitors, and even direct requests for a quote - but conversion to sales is low. What’s going on? It can be tempting to point fingers, but this is almost always a system problem more than any particular team's failing. Here’s a checklist to help diagnose.
In many industries, sales is used to ‘selling’ the vision of the product in advance of it being built, and customers assume vapourware by default. No one bats an eye because we’re accustomed to the idea that engineering will always be able to fulfill whatever we’re selling, given enough time and money.
New technologies like machine learning and blockchain offer a world of possibilities, but many of these possibilities may not actually be able to be implemented in practice, even with a huge budget. It's easy to promise "The product will automatically predict X with high accuracy." where X could be anything from detecting a security breach to predicting stock prices to finding the perfect outfit for you wear. But even if the prototype is already 70% accurate, it may never get to 80%, or whatever you need it to be to be commercially viable. A Program Manager is responsible for managing multiple interrelated projects and ensuring that - taken together - they produce specific business outcomes and benefits for an organization.
The title "Program Manager" is not very common. Organizations have Project Managers, Product Managers, General Managers. But "Program Manager" is rare. This is because often executives and middle managers play the role of Program Manager even if they don't have the title. Most companies are laser-focused on meeting the current quarter's target, with an all-hands-on-deck effort by sales, marketing and product to close the gap by quarter-end. There is usually also a funnel of opps and leads for next quarter. But what about 2 quarters out?
Short-term revenue is the lifeblood of the company - you don't survive very long if you don't make your number. So companies get good at meeting their target quarter-to-quarter. But one day the current quarter does not look good. The funnel is just not there. Maybe you've saturated the market, or there's been a disruption, or maybe you just didn't have enough funnel-generating activity 6 months ago. Now you're in trouble, and no amount of short-term execution can solve it. Don't fall into this trap! AI/ML has the potential to deliver incredible value to customers. A single breakthrough can make a product company's growth soar. A fine-tuned model can completely transform an enterprise's operations.
The mechanics of delivering such a program are very similar to traditional projects on the face of it, so it is tempting to think of the implementation as being the easy part. But because of the non-deterministic nature of AI/ML, all the pitfalls of ordinary software development programs - misaligned objectives, underestimation, lack of process, skimping on QA, ignoring risks, etc. - are amplified x10. To deliver successfully, you need to ratchet up the program diligence. Traditional data protection has been about securing data behind the corporate perimeter, locking down IT systems and endpoints with firewall and data loss prevention (DLP) technology. Now there is an increasing recognition that traditional data protection is not working. Faced with the new realities of cloud, shadow IT, BYOD, increasing collaboration with 3rd parties, and “last mile” endpoints like USB devices… no matter how well you secure data behind the perimeter, your data will eventually leak.
In their DLP magic quadrant analysis, Gartner said “At present, even with extensive DLP coverage across endpoints, networks and data repositories, there are still gaps and data flows where data can leak. The better answer is a data security strategy focused on securing the data itself, as opposed to trying to secure every system that comes in contact with sensitive data.” What Gartner is talking about is a revival of Digital Rights Management (DRM) technology, that embeds encryption directly in a company’s valuable data assets themselves – their sensitive files and e-mails – so that even if the data does leak beyond the perimeter, it’s still protected. Much like AI and Blockchain, Digital Rights Management technology is an extremely attractive concept that has had implementation challenges, but is now starting to overcome those implementation obstacles to go mainstream, most notably Microsoft Azure Information Protection (AIP). Here’s a look at what to expect. "How would you feel if you couldn't use the product anymore?" According to growth hacking pioneer Sean Ellis, this is the question to ask to determine your level of product-market fit. In response, you are looking for at least 40% of your customer base who say they would be "very disappointed". This represents user passion.
Read any article on product/market fit and it will say "Talk to customers and focus on their problems. It took us 2 years but we found our product/market fit and sold for $X!". One thing? Simple! Talk to customers.
But there's a startling lack of practical guides on how to actually talk to customers to elicit and qualify pain points. And there are so many false pains that you can latch on to in customer conversation if you don't know what you're doing (which may explain why that article invariably says "it took us 2 years to find what customers wanted"). Let's look at the reasons why actually getting to a real customer pain point is so hard, and how to do it right. Companies that have no connection to the financial world - Mindbody (fitness), ServiceTitan (HVAC, plumbing), WonderSchool (daycare), Jobber (lawncare, painting) - are suddenly making more revenue from online payments and other financial services than they do from their core software subscription revenue.
This is because new Fintech infrastructure companies have made it possible for SaaS businesses to add financial services alongside their core software product. By adding Fintech, SaaS businesses can increase revenue per customer by 2-5x, according to an a16z analysis, a significant new market opportunity and indicator for what might be to come in the future. "Know your audience". "Understand the buyer." "Be customer-centric." The key to lead generation and growth has been in MBA 101 textbooks since the dawn of time.
These 101 textbooks also say to capture the relevant information about your target buyer in the forma of a persona. But the vast majority of teams don't actually create personas, or use them in the right way. Ten years ago, as long as you had a great product idea, growing a tech business was straightforward. But today the market has reached a level of noise that even the best products can't cut through. The average person sees 3,000 ads a day. Promotional channels from Google SEO to Facebook to Amazon are saturated and in constant flux. How do you cut through the noise?
|